2.1 Starting the virtual machine
2.1 开启虚拟机
I created a special virtual machine to run the examples. This will save you a lot of time installing stuff.
我创建了一台特殊的虚拟机以运行这些示例。这将为你安装实验环境节省很多时间。
You need the latest version of Vagrant to run the code (1.7+). Get it from here.
你需要最新版本的Vagrant以运行示例代码(1.7+)。从这里获得它。
http://www.vagrantup.com/downloads.html¹
You will need to get the latest code from Github. If you are on Windows, I recommend the excellent and easy to use Github client².
你将需要从GitHub获得最新的代码。如果你在Windows平台上,我推荐杰出并且易用的GitHub client。
After that, get the code from: https://github.com/shantnu/PythonForHackers
在那之后,从https://github.com/shantnu/PythonForHackers获得代码。
If you don’t want to install Git, you can still get the code. Github allows you to download the code as a zip file:
如果你不想安装Git,你仍然可以获得代码。GitHub允许你以zip文件的格式下载代码。
 Anyway you want, download the code into a directory. Open a command prompt there and type:
Anyway you want, download the code into a directory. Open a command prompt there and type:
使用任何你希望使用的方法,将代码下载至一个目录。在这个目录中打开一个命令提示符窗口并输入:
vagrant up
This will start the virtual machine I created. It installs a Ubuntu 14.04 VM. If you don’t have the Ubuntu image, it will download it from the web, and that might take some time.
这将开启我创建的虚拟机。此命令将会安装一台Ubuntu 14.04虚拟机。如果你没有Ubuntu镜像文件,他将会从web上下载它,并且那将花费一些时间。
Once the virtual machine has been installed, type:
一旦这台虚拟机已经被安装完毕,输入:
vagrant ssh
If you are on Windows, you might need the ssh utility installed. There are many ways to do so. If you installed the Github client, it also comes with a ssh client. Make sure it is in the path. I prefer to use Cygwin (a Linux like command line emulator), but you don’t need it.
如果你在Windows平台上,你可能需要安装ssh程序。这里有很多方法可以实现。如果你安装了Github client,它会同时安装一个ssh client。确保它被写入path中。我倾向于使用Cygwin(一个类Linux命令行模拟器),但是你不需要它。
If all goes well, you should now be in the virtual machine.
如果一切都进行的顺利,你现在应该在虚拟机里。
To start off, run the main Flask app:
为了开始,运行主Flask app程序:
cd /vagrant
./app.py &
The & sign means it will be started in the background, so you can continue running other commands.
&符号表示程序将在后台被运行,这样你可以继续运行其他命令。
To view the web app, open up your web browser and go to this link: http://127.0.0.1:5000³
打开你的web浏览器并且打开此链接http://127.0.0.1:5000³以查看web app。
I created a special web app for you to practice hacking, because you may be shocked to know (yes, shocked!) that most modern frameworks prevent most attacks by default. If you tried any of these hacks on a normal Django or Flask webapp, they wouldn’t work (or they might! The programmer may not have been paying attention. Hopefully, you will pay attention after reading this book).
我为你创建了一个特殊的web app以供练习hacking,因为你可能震惊的发现(对,震惊!)大多数现代框架用default阻挡大多数攻击。如果你在一个普通的Django或Falsk webapp上尝试这些攻击,它们行不通(也许能行!程序员也许没有注意。希望在读过这本书后你会注意)。
As I have said before, you don’t need to understand how the web app works, though it isn’t that complex. It is one step above the Flask Hello World project. Instead of explaining to you how the whole app works, I’ll just go over the relevant parts, so you can mess around with the code, if you so want.
正如我之前说过的,你不需要理解web app是怎么工作的,尽管那并不复杂。这比Flask Hello World项目高了一步。我会直接讲相关的部分而不是向你解释整个app是如何工作的,这样你可以随意修改代码。
Okay, so we saw the login page above. The relevant part of the app that loads that page is:
好,我们看到了login页面。加载该页面的应用程序的相关部分是:
@app.route('/', methods=['GET', 'POST'])
def login():
error = None
if request.method == 'POST':
if request.form['username'] == "Perry.Platypus" and request.form['password'] == 'ilovefish':
return redirect(url_for('user_data', user="user1"))
else:
error = "Wrong username or password, dude"
return render_template("login.html", error=error)
Don’t worry if you can’t follow the above. The only important bit is this line:
如果你不能理解以上代码,不要担心。唯一重要的是这行:
if request.form['username'] == "Perry.Platypus" and request.form['password'] == 'ilovefish':
return redirect(url_for('user_data', user="user1"))
else:
error = "Wrong username or password, dude"
This tells us what user name and password the form is expecting. Yes, I know. Not very high tech.To start off, let’s try to enter the password manually. First, enter the correct username and password:
这告诉我们表单期望的用户名和密码。是,我知道。不是什么高科技。开始吧,让我们试着手动输入密码。首先,输入正确的用户名和密码: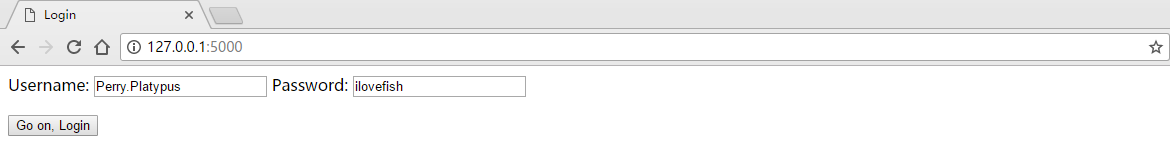 And we reach this screen:
And we reach this screen:
然后我们到了这个页面: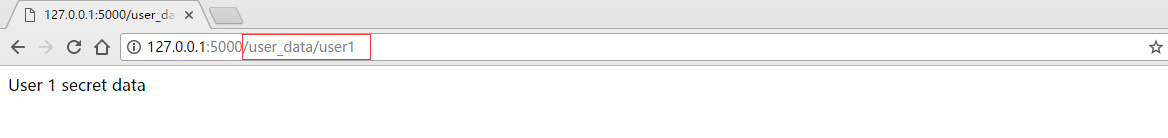 Yes, there isn’t a lot there. In a normal webapp, this would contain your secret data, the stuff you want hidden. Also look at the webapp route. Specifically, the part I have circled red.
Yes, there isn’t a lot there. In a normal webapp, this would contain your secret data, the stuff you want hidden. Also look at the webapp route. Specifically, the part I have circled red.
是的,那里没有太多东西。在一个普通的webapp中,它会包含你的秘密数据,你想隐藏的东西。再看看webapp的路径。具体来说,是我用红色圈出的部分。
You can see that the data for user1 is stored under the path of user1. This is very bad security practice, and we will come back to this. But for now, go back to the home page, and enter a wrong password:
你可以看到user1的数据被存储在user1的路径下。这是非常糟糕的安全实例,我们以后将回到这一点。但是现在,回到主页,输入一个错误的密码: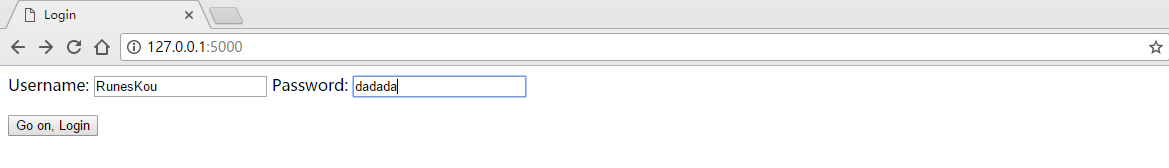 and you get the error message you saw earlier in the code:
and you get the error message you saw earlier in the code:
然后你就收到了你之前在代码里看到过的错误信息。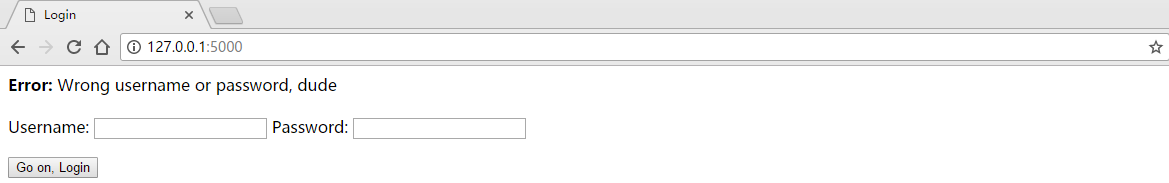 Okay, now you could sit there trying different usernames and passwords (remember, in the real world you won’t have access to the source code. And hopefully, the programmer won’t store the password in plain text anyway! Look at the section on on how to store passwords safely).
Okay, now you could sit there trying different usernames and passwords (remember, in the real world you won’t have access to the source code. And hopefully, the programmer won’t store the password in plain text anyway! Look at the section on on how to store passwords safely).
好了,现在你可以坐在那里尝试不同的用户名和密码了(记住,在现实世界中,你无法访问源代码。但愿程序员不会把密码存储在纯文本中!阅读关于如何安全地存储密码的章节)。
Or you could write a script to automate the attacks.
或者你可以写个脚本将攻击自动化。
You will have to guess two things: The username, and the password.
你将不得不猜测两个东西:username和password。
The password, we will get from a dictionary.
我们将从一个字典中获取password。
User names are harder, but I have assumed this is a corporate website, and many corporations have the username of the type: FirstName.LastName. So for me (Shantnu Tiwari), the username would be Shantnu.Tiwari .
用户名比较困难,但我已经假设这是一个公司网站,很多公司都有这个类型的用户名:FirstName.LastName.所以对我(Shantnu Tiwari)来说,用户名可能是是Shantnu.Tiwari。
If you don’t have access to this info, you will have to guess the username as well. Which, while comparatively(相对地) harder, isn’t that complicated overall, as usernames are also chosen(usually) by some logic. So for someone called John Doe, the usernames could be [email protected], [email protected] (date of birth), [email protected] (the year he created the email id), and so on. It will require another dictionary for the usernames, but that is generateable using a script.
如果你不能访问这个信息,你也需要猜测用户名。虽然比较难,但总体上并不复杂,因为用户名也根据一些逻辑被选择(通常是)。
因此,对于一个叫John Doe的人来说,用户名可以是[email protected],[email protected](出生日期),[email protected](他创建这个电子邮件id的日期),等等。这将需要另一个用于username的字典,但这是可以使用脚本生成的。
We will keep it simple and use the corporate scheme; as hacking corporate websites is more profitable anyway, comparing to hacking some email provider no one uses. Hello, AOL! (Actually, I’m told AOL dialup still has hundreds of thousands of users in America).
我们将保持它的简单性并使用公司计划;;不管怎么说,与攻击一些没有人使用的电子邮件提供商相比攻击公司网站的利润更高。你好,美国在线(AOL)!(事实上,我被告知AOL拨号在美国还有成千上万的用户)。
If you look in the /vagrant directory, there are two files. The first is names.txt :
如果你查看/vagrant目录,那里有两个文件。第一个叫names.txt 。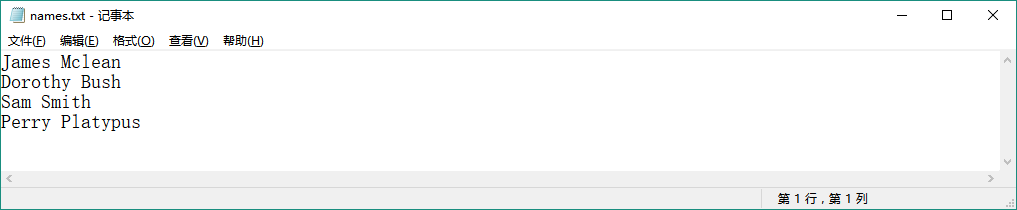 This contains a few made up names, including, you will notice, our username.
This contains a few made up names, including, you will notice, our username.
它包括一些编造的名字,你会注意到,包括我们的username。
There is another files called dictionary.txt:
那里还有一个叫dictionary.txt的文件: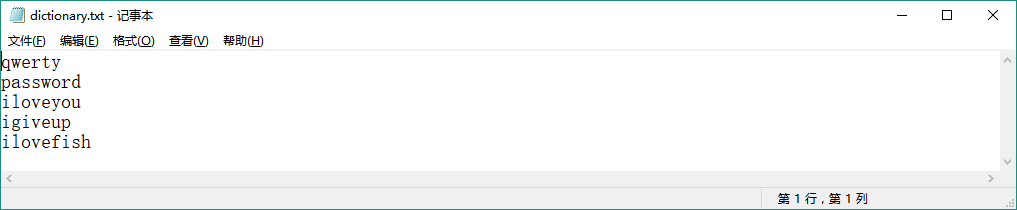 This is a toy dictionary ,of course. A real dictionary will have millions of entries for all the common passwords. And then you have Rainbow Tables, which are a completely new game (we will discuss them in the section on passwords).
This is a toy dictionary ,of course. A real dictionary will have millions of entries for all the common passwords. And then you have Rainbow Tables, which are a completely new game (we will discuss them in the section on passwords).
当然,这是一本来搞笑的字典。一个真正的字典将有数百万个条目可用于所有常用的密码。然后你就有了彩虹表,那将是一个全新的游戏(我们将在passwords章节讨论它们)。
Our task is to create usernames from our names.txt file, and try all the dictionary passwords with them.
我们的任务是从我们的names.txt文件中创建用户名,并对它们尝试所有的字典密码。
By the way, if you are thinking that having a list of names which can be used for hacking sounds unbelievable, this has happened in real life. Certain hackers managed to get an old employee directory and tried this exact attack. They even called all the numbers in the directory to check the names were up to date. So employees got a call like, Hello, what’s your name?, and the caller hung up after getting the name. S/he was only interested in getting usernames, as they already knew this company used the FirstName.LastName method.
顺带一提,如果你认为有一串可以用于攻击的名字这件事听起来难以置信,这在现实生活中已经发生了。某些黑客设法获取了一个旧的员工目录并尝试了这种精确的攻击。他们甚至打给目录中的每个成员以检查名单是不是最新的。所以员工们接到了一个像这样的电话“你好,你叫什么名字?”,并且打电话的人在获得姓名后马上挂掉电话。她/他只对用户名感兴趣,因为他们已经知道这家公司使用FirstName.LastName的格式。
Luckily, in this case, IT caught on to them and temporarily shut off their servers till they could apply patches. And that’s the only reason you haven’t heard of this attack.
幸运的是,在这种情况下,IT人员察觉了这些攻击并且暂时关闭了他们的服务器直到它们可以打补丁。这是你没有听说过这次袭击的唯一原因。